In short: Microsoft Teams iOS client login screen can be bypassed after organization mandated login (refresh token) expiration has expired by dismissing the login view and tapping on the enabled user-interface elements. This behavior can be repeated an unlimited amount of times to browse section of the app and view protected data meant for a successfully authenticated user.
- Expiration example: Organization mandates re-authentication period of 18 hours. The user is no longer authenticated 19 hours after initial login.
- Cached data such as notification, teams, and chat are available.
- New Teams voice calls can be successfully joined with two way voice communication.
- The only thing needed for this is quick fingers.
Click above image for video version of PoC screen recording.
This behavior can be viewed in the iOS Microsoft Teams app on at least version 2.3.1 (tested working on 03MAR21). I have not tested this on the equivalent Android Teams app. Steps to access user data after your login expires are below:
-
Login to MS Teams account under an organization with a relogin (refresh token) expiration time of N. (Ex: Max lifetime of refresh token of 18 hours) MS Teams may be set to use a authentication method similar to OAuth 2.0.
-
Wait N hrs for the refresh token to expire.
- Open Teams iOS app. iOS client app will popup webview loading a login page at https://login.microsoftonline.com/XXX/oauth2/v2.0/authorize.
- Before the login webview popup, the iOS client will find that the refresh_token is expired by a response from a request to https://login.microsoftoline.com/XXX/oauth2/v2.0/token.
- See OAuth 2.0 for details on the Authorization Code grant type login flow.
-
Click “Cancel” button in upper-left of the popup webview containing login page. The popup webview will dismiss by sliding down off the screen.
- Full interaction and information viewing is possible in the iOS client app for a brief period. Examples of tested data access: - Bottom tab bar can be clicked to view different Teams data such as notifcations, chats, calendar. - Pull to refresh on notifications view will intiate a refresh and load new data - Clicking “join” meeting on calendar view will successfully join a team meeting and audio. (connection to api.flightproxy.teams.microsoft.com made) Creation of the meeting is logged and can be seen in the “chat” view of an event showing who entered the meeting.
-
iOS client app may display a dialog indicating auth failure and an option to sign out. Click “cancel”. iOS client app will popup the login webview again.
-
Go to step 4. Repeated user privileged data access is possible by cancelling the popup login webview and tapping on parts of the graphical user interface during the few seconds before the login alert and webview pop up again.
This login bypass and information disclosure vulnerability was submitted to Microsoft and assigned case #63474. Screen recordings demonstrating bypass of the login screen and ability to successfully join a call were shared as well. A month later, Microsoft replied that this “behavior is considered to be by design”.
We determined that this behavior is considered to be by design because after the tokens expire, the device still has cached data locally which is accessible to the Teams client.
Caching data locally to alleviate the need to redownload user Teams data is a normal design philosophy. However, the graphical user interface should not be designed to allow free access to cached data once the user access to the data is known to be expired/invalid. The separate data storage and data presentation functionalities of the Microsoft Teams iOS client application should be designed to mask or hide the cached data from view until the user has successfully reauthenticated.
Microsoft’s response also suggests that being able to join, speak, and hear Teams calls when not authenticated is expected behavior.
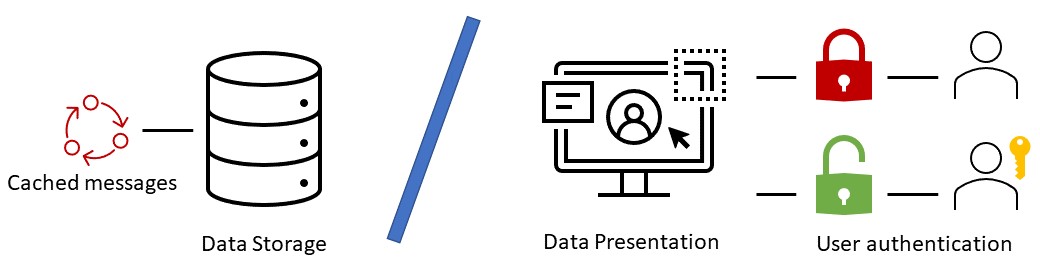
A simple and effective solution would hide visibility of the main Teams user interface when the user authentication has expired. Once the user has successfully reauthenticated, enable interaction and make the main GUI containing cached user data visible again. The Teams call infrastructure should also be patched to check if the authentication has expired before allowing a client to join a call.
If this is apparently intended functionality - maybe a helpful feature to peek at messages and join Teams calls when the user’s authentication is not verified - people should know more about the functionality of “Quick Fingers” when the user “forgets” their password.
01FEB21 - Reported bug to Microsoft Security Response Center (MSRC) Researcher Portal
02MAR21 - MSRC informs me that login bypass and information disclosure described is unavoidable “by design”.

